IAM Roles for EC2 - Overview
IAM Roles for EC2
allow you to access Amazon S3 storage from EC2 without transferring your Access Key ID and Secret Access Key to the instance.
You define the Role in your IAM AWS Console
and launch the EC2 instance with this role. Applications running on such instance are now able to obtain temporary Access Keys
from instance metadata. These access keys are rotated during the day providing you an additional layer of security.
To connect to Amazon S3 from EC2 via IAM Role:
1. Start S3 Browser and click Accounts -> Add New Account.
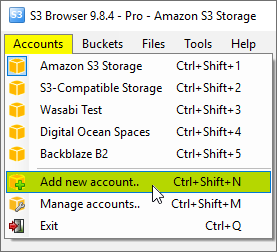
Click Accounts -> Add New Account
Add New Account dialog will open:
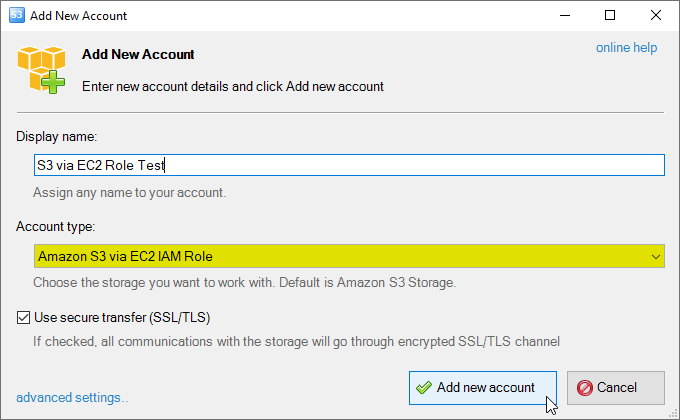
Add New Amazon S3 from EC2 via IAM Role Account dialog
2. Enter Account Name - any name of your choice to label the account.
3. Choose Amazon S3 on EC2 via IAM Role as Account Type.
4. Click Add new account.
You can now choose the newly added account from the accounts menu:
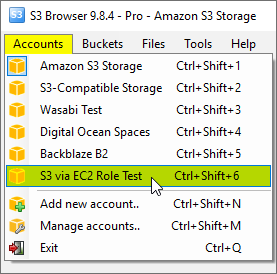
Click Accounts -> Account Name to switch between accounts.
Advanced Account Settings
You may also configure additional settings when adding new or editing existing account.
In order to open advanced account settings, please click the advanced settings link
located at the bottom left corner of the dialog.
The Advanced Account Settings dialog will open:
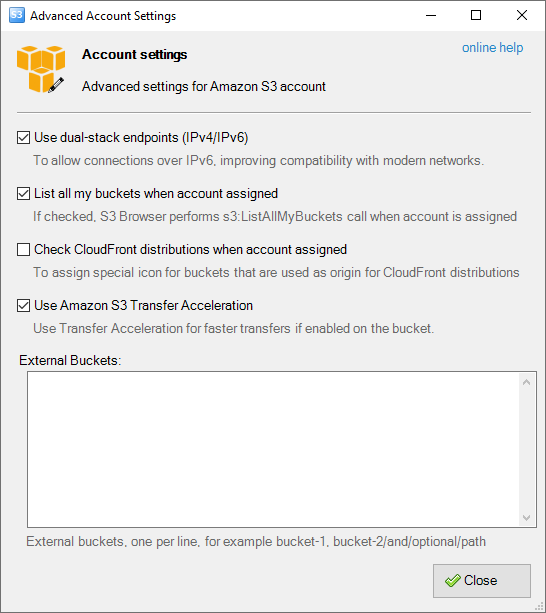
Advanced account settings
You may configure the following settings here:
Enable Dual-Stack Endpoints (IPv4/IPv6) - When checked, S3 Browser will use dual-stack endpoints
to access storage, allowing connections over both IPv4 and IPv6.
This improves compatibility with networks that support IPv6.
List All My Buckets When Account Assigned - When checked, S3 Browser will perform the
s3:ListAllMyBuckets call when the account is assigned. If the account does not have permission
to list all buckets, you can uncheck this option to avoid failed tasks and warnings in the log.
Check CloudFront Distributions When Account Assigned - When checked, S3 Browser will perform the
cloudfront:ListDistributions call when the account is assigned, allowing it to set a special
icon for buckets used as origins for CloudFront distributions. If the account does not have permission to
list CloudFront distributions, you can uncheck this option to avoid failed tasks and warnings in the log.
External Buckets - You can edit the external buckets associated with the account. Each bucket should be listed on a new line.
Optional paths are also supported, with a slash used as the delimiter (e.g., my-bucket/and/optional/path).
|

