How to access S3 via Temporary Security Credentials
An AWS Account or an IAM user can request temporary security credentials and use them to access Amazon S3.
The credentials consist of an Access Key ID, a Secret Access Key, and a Security Token.
Temporary security credentials are obtained from AWS Security Token Service (AWS STS) by sending the
AssumeRole
or GetSessionToken call.
With S3 Browser you can easily work
with Amazon S3 via temporary security credentials, it calls AssumeRole
or GetSessionToken
automatically when required.
Once obtained, temporary security credentails are cached in memory and used until they expire,
then the next STS call is sent.
To connect to Amazon S3 via AssumeRole
1. Start S3 Browser and click Accounts -> Add New Account.
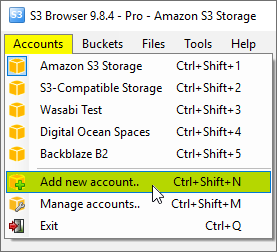
Click Accounts -> Add New Account
The Add New Account dialog will open:
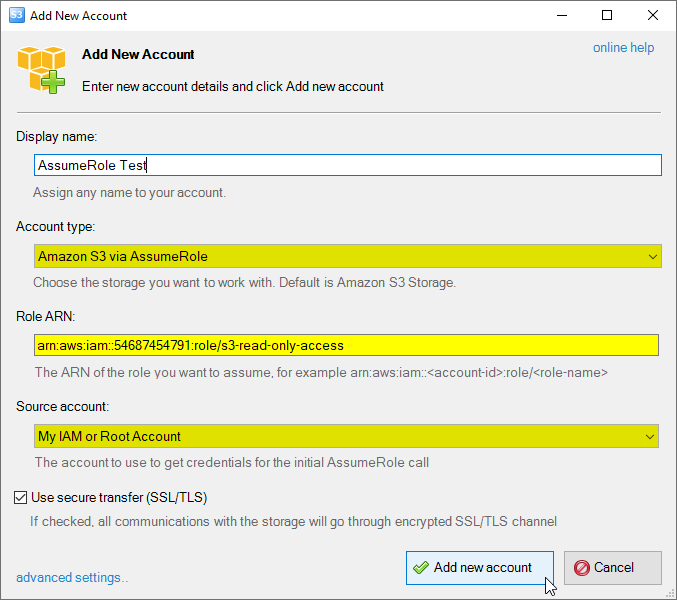
The Add New Account dialog.
2. Choose the Amazon S3 via AssumeRole account type
3. Specify the Role ARN - The Amazon Resource Name of the role to assume.
4. Select the Source Account - the account to send the AssumeRole request.
5. Turn on the Use secure transfer (SSL/TLS) checkbox if you would like to encrypt all communications with the storage.
6. Click Add new account
You can now choose the newly added account from the Accounts menu:
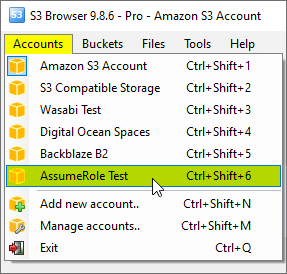
Click Accounts -> Account Name to switch between accounts.
Advanced Settings
You can also configure additional settings for the Amazon S3 via AssumeRole account type.
To open Advanced Settings please click the Advanced settings.. link located at the bottom-left corner of the dialog.

Click the Advanced settings.. link
The Advanced Account Settings dialog will open:
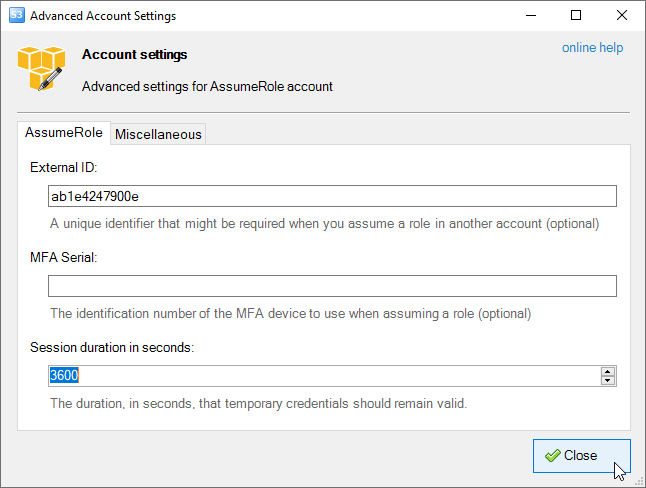
Advanced account settings, the AssumeRole tab.
AssumeRole
1. External ID - an optional field, a unique identifier that might be required when you assume
a role in another account. If the administrator of the account to which the role belongs provided
you with an external ID, then specify that value here.
2. MFA Serial - an optional field, the identification number of the MFA device that is associated
with the user who is making the AssumeRole call. Specify this value if the trust policy of the role being
assumed includes a condition that requires MFA authentication.
3. Session duration in seconds - the duration, in seconds, that temporary credentials should remain valid.
4. Session name - an identifier for the assumed role session. This field helps to track individual sessions.
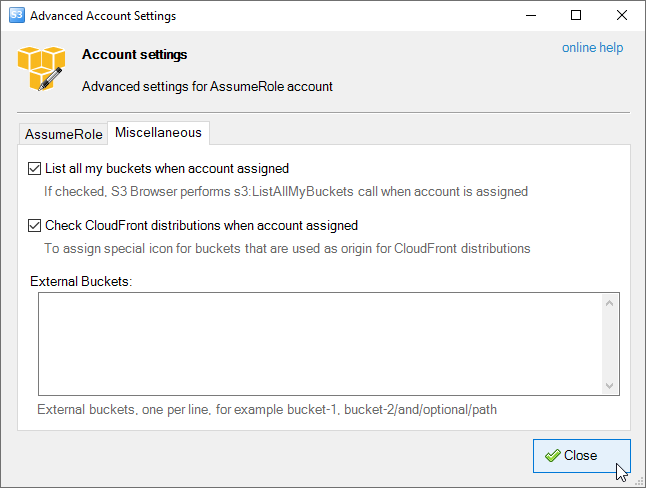
Advanced account settings, the Miscellaneous tab.
Miscellaneous
Enable Dual-Stack Endpoints (IPv4/IPv6) - When checked, S3 Browser will use dual-stack endpoints
to access storage, allowing connections over both IPv4 and IPv6.
This improves compatibility with networks that support IPv6.
List All My Buckets When Account Assigned - When checked, S3 Browser will perform the
s3:ListAllMyBuckets call when the account is assigned. If the account does not have permission
to list all buckets, you can uncheck this option to avoid failed tasks and warnings in the log.
Check CloudFront Distributions When Account Assigned - When checked, S3 Browser will perform the
cloudfront:ListDistributions call when the account is assigned, allowing it to set a special
icon for buckets used as origins for CloudFront distributions. If the account does not have permission to
list CloudFront distributions, you can uncheck this option to avoid failed tasks and warnings in the log.
External Buckets - You can edit the external buckets associated with the account. Each bucket should be listed on a new line.
Optional paths are also supported, with a slash used as the delimiter (e.g., my-bucket/and/optional/path).
|

