Bucket Policies allow you to create conditional rules for managing access to your buckets and files.
With bucket policies, you can also define security rules that apply to more than one file,
including all files or a subset of files within a bucket. This makes updating and managing permissions easier!
To Edit Amazon S3 Bucket Policies:
1. Click Buckets, Edit Bucket Policy:
You can also use Ctrl+O keyboard shortcut to open Bucket Policies Editor.
The Bucket Policy Editor dialog will open:
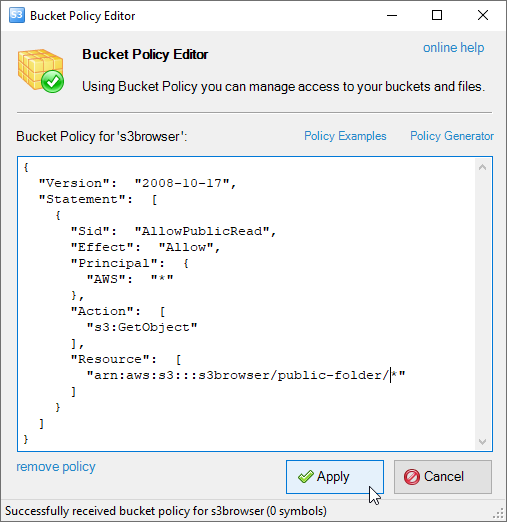
Bucket Policies Editor allows you to Add, Edit and Delete Bucket Policies.
2. Enter valid Amazon S3 Bucket Policy and click Apply Bucket Policies.
See some Examples of S3 Bucket Policies below and
Access Policy Language References for more details.
How to grant public-read permission to anonymous users (i.e. to everyone)
{
"Version": "2008-10-17",
"Statement": [
{
"Sid": "AllowPublicRead",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": [
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::my-brand-new-bucket/*"
]
}
]
}
How to grant full access for the users from specific IP addresses.
{
"Version": "2008-10-17",
"Id": "S3PolicyId1",
"Statement": [
{
"Sid": "IPAllow",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": "s3:*",
"Resource": "arn:aws:s3:::my-brand-new-bucket/*",
"Condition": {
"IpAddress": {
"aws:SourceIp": "192.168.143.0/24"
},
"NotIpAddress": {
"aws:SourceIp": "192.168.143.188/32"
}
}
},
{
"Sid": "IPDeny",
"Effect": "Deny",
"Principal": {
"AWS": "*"
},
"Action": "s3:*",
"Resource": "arn:aws:s3:::my-brand-new-bucket/*",
"Condition": {
"IpAddress": {
"aws:SourceIp": "10.1.2.0/24"
}
}
}
]
}
How to protect your amazon s3 files from hotlinking.
{
"Version": "2008-10-17",
"Id": "preventHotLinking",
"Statement": [
{
"Sid": "1",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::my-brand-new-bucket/*",
"Condition": {
"StringLike": {
"aws:Referer": [
"http://yourwebsitename.com/*",
"http://www.yourwebsitename.com/*"
]
}
}
}
]
}
How to allow only specific IP to write to a bucket and everyone read from it.
{
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::my-brand-new-bucket/*",
"Condition": {
}
},
{
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": [
"s3:PutObject",
"s3:DeleteObject"
],
"Resource": "arn:aws:s3:::my-brand-new-bucket/*",
"Condition": {
"IpAddress": {
"aws:SourceIp": "192.168.0.0/16"
}
}
}
]
}

